Introduction
Our team goes beyond the scope of OWASP Top 10, OWASP Mobile Top 10 and performs an assessment that pushes the boundary for application security. We don’t solely scan the application for known bugs but leverage extensive research to identify deep technical vulnerabilities.
Types of Mobile Applications
Native Applications
A native application is developed for use on a particular platform or device. Native apps can provide optimized performance and take advantage of the latest technology, such as a GPS, compared to web apps or mobile cloud apps developed to be generic across multiple systems.
Mobile Web Applications
Mobile web applications, also known as progressive web apps (PWA) are Internet-enabled apps that have specific functionality for mobile devices. They’re accessed through the mobile device’s web browser and they don’t need to be downloaded and installed on the device.
Hybrid Applications
Hybrid apps are a combination of web-based content and native components accessing services on the mobile device, most notably, storing or using storage. These are web apps built into the native mobile framework and take advantage of the cross-compatibility of web technologies, such as HTML5, CSS, and JavaScript.
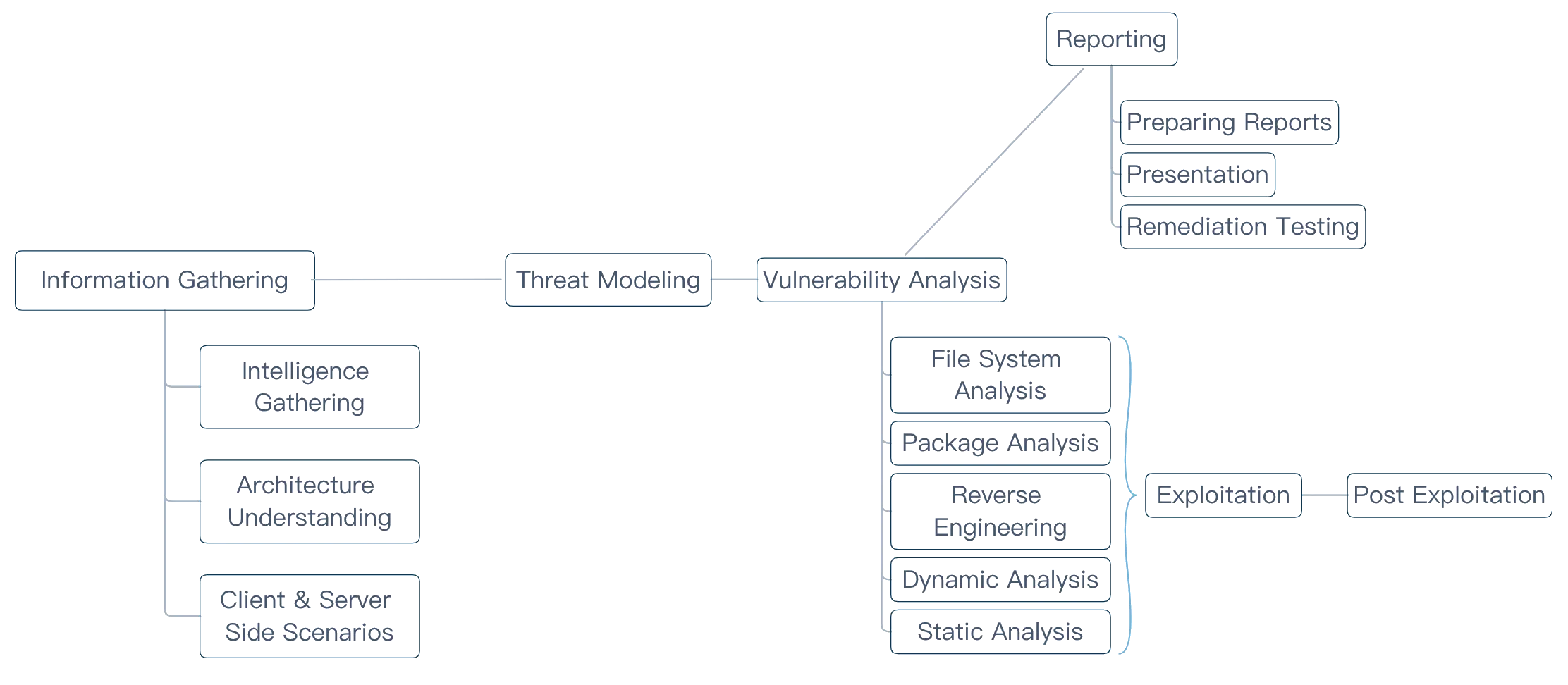
Methodology
Automated
Intect will identify the vulnerabilities present in the application with the help of automated tools and eliminate the false-positives. Automated scanners will give us an overview of the possible existence of vulnerabilities in the environment.
Manual
Our analyst will identify every exploitable vulnerability present in the application. We will check for logical flaws which might compromise authentication/authorization, injection attacks, data security, input validations, session management issues, etc. We also fetch every open port and the services running on the APIs’ servers. After that, we test them for vulnerabilities depending on their level of exploitability and availability on the environment they exist.
Types of Testing
Black Box
Black-box testing is a method of software/application testing that examines the functionality of an application without knowing it’s internal/backend working. It requires no prior knowledge of the application or the intervention of the application vendor.
Grey Box
In grey-box assessment, typically, the auditor has some knowledge of the application which is given by the business owners in form of application walk-throughs, application data flow, API documentation, etc. The purpose of grey-box assessment is to provide a more efficient & focused security assessment.
Assessment Phases
Traffic Analysis
Traffic analysis is performed while executing the application by observing the APIs or services used to send data back and forth. This can also help spot configuration mistakes and errors and identify other specific problems with applications.
| High Level Controls | |
| Authentication & Authorization | The controls in this group evaluate the application against weak passwords, insecure password recovery mechanisms, poorly protected credentials or lack of granular access control to access a particular interface. |
| Token Management | The controls in the groups are checked against the security of token i.e token theft due to MITM. |
| Password Management | The controls in this group evaluate the practices implemented for storing and managing passwords to prevent unauthorized access. |
| Data in Transit | The controls in this group protect the security of data in transit by mapping controls related to encryption and SSL/TLS protocols such as HTTPS, FTP, etc. |
| User Input Handling | The vulnerabilities in this group cover the security of the data against the malicious user inputs. |
| Business Logic Flaws | The vulnerabilities in this group are checked against the misuse of an application by circumventing the business rules i.e ways of using legitimate processing flow of an application in a way that results in a negative consequence to the organization. |
Static Analysis
Static Analysis is performed mostly without executing the application by looking at the application files and code present on the device.
Local Storage Analysis is performed to inspect various types of files that can potentially store sensitive information in mobile’s local storage in the form of plain text, files, databases, web cache, etc.
Binary Analysis
This analysis analyzes the raw binaries that compose a complete application, which is especially helpful when there isn’t access to the source code.
| High Level Controls | |
| Data Security | Vulnerabilities in this group cover the validation of the data at-rest i.e hard coded sensitive data, user PII information, decision making in the application. |
| Source Code Analysis | The vulnerabilities in this group cover the secure coding best practices or developer guidelines issued by Google/Apple. Furthermore, would evaluate for the hardcoded sensitive data, data encryption keys or initialization vector or salts. |
| Application Integrity Analysis | This control validate the application against the tampered code, 3rd party libraries or application assets modifications and also validates if the application server responds to the tampered application or not. |
| Application Misconfiguration | Manifest file and other configuration files are evaluated manually for the application misconfiguration. |
| Cryptographic Controls | The cryptographic controls help an auditor to find the usage of weak cryptographic algorithms used throughout the application i.e encryption, encoding, hashing algorithms. |
Runtime Analysis
| High Level Controls | |
| Access Control | The authorization and the business logic decisions in the application are evaluated based on the controls in this group. |
| HTTP Security | Controls in this group evaluate the usage of various HTTP methods whenever data is sent to or received from the application server. |
| Data Protection | Vulnerabilities in this group covers the validation of the data sent to or received from the server along with the validation of the data stored at client side i.e user PII information, key exchange, data tampering, etc. |
| Logging | Controls in this group covers the validation of sensitive data, HTTP requests / response stored in the local data storage or in the application runtime logs. |
| Token Management | Controls in this group cover whether the user specific tokens are used for the client server communication or not. Further, Intect would also check for token randomization, expiration. |
| User Input Handling | The vulnerabilities in this group check for the business logic decisions based on user input in the application. |
| Error Handling | The error handling section covers the information disclosure vulnerability that arises due to the lack of user input sanitization i.e. improper exception handling. |
| Reverse Engineering | Reverse Engineering is performed on the applications which deploy various security mechanisms such as Client-Side Encryptions, Root/Jailbreak detection, SSL Pinning. Such client-side controls may be bypassed by deconstructing the binary and related files. The process is time-consuming and tedious and hence requires effort for the project to be calculated accordingly. |