Introduction
Thick client pentesting involves both local and server-side processing and often uses proprietary protocols for communication.
Simple automated assessment scanning is not sufficient and testing thick client applications requires a lot of patience and a methodical approach. Moreover, the process often requires specialized tools and custom testing setup.
Architecture of Thick Client
Two-Tier architecture
In two-tier architecture, the thick client application implements a client-to-server communication. The application is installed on the client computer and, in order to work, will need to communicate with a database server. For example, imagine an HR application that was installed on the client computer and, in order to retrieve the employees’ information, communicates directly with the HR database server.
Three-Tier architecture
In three-tier architecture, the client communicates with an application server, which in turn talks to the database in a manner similar to a regular web application. The most common communication method in these applications may be carried out using HTTP/HTTPS.
Three-tier architecture has a security advantage over two-tier architecture, because it prevents the end-user from communicating directly with the database server.
Methodology
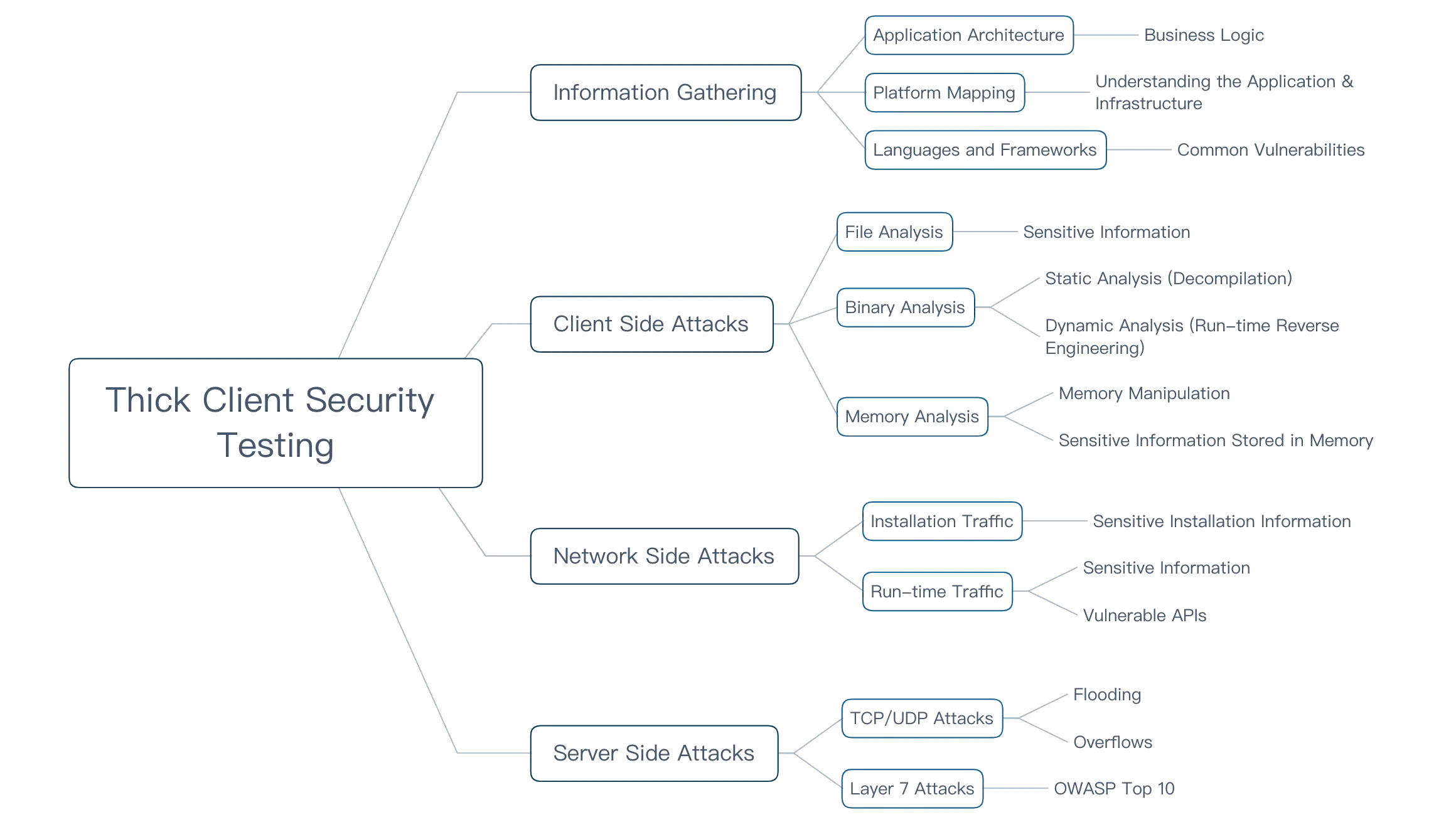
Types of Testing
Black Box
Black-box testing is a method of software/application testing that examines the functionality of an application without knowing it’s internal/backend working. It requires no prior knowledge of the application or the intervention of the application vendor.
Grey Box
In grey-box assessment, typically, the auditor has some knowledge of the application which is given by the business owners in form of application walk-throughs, application data flow, API documentation, etc. The purpose of grey-box assessment is to provide a more efficient & focused security assessment.