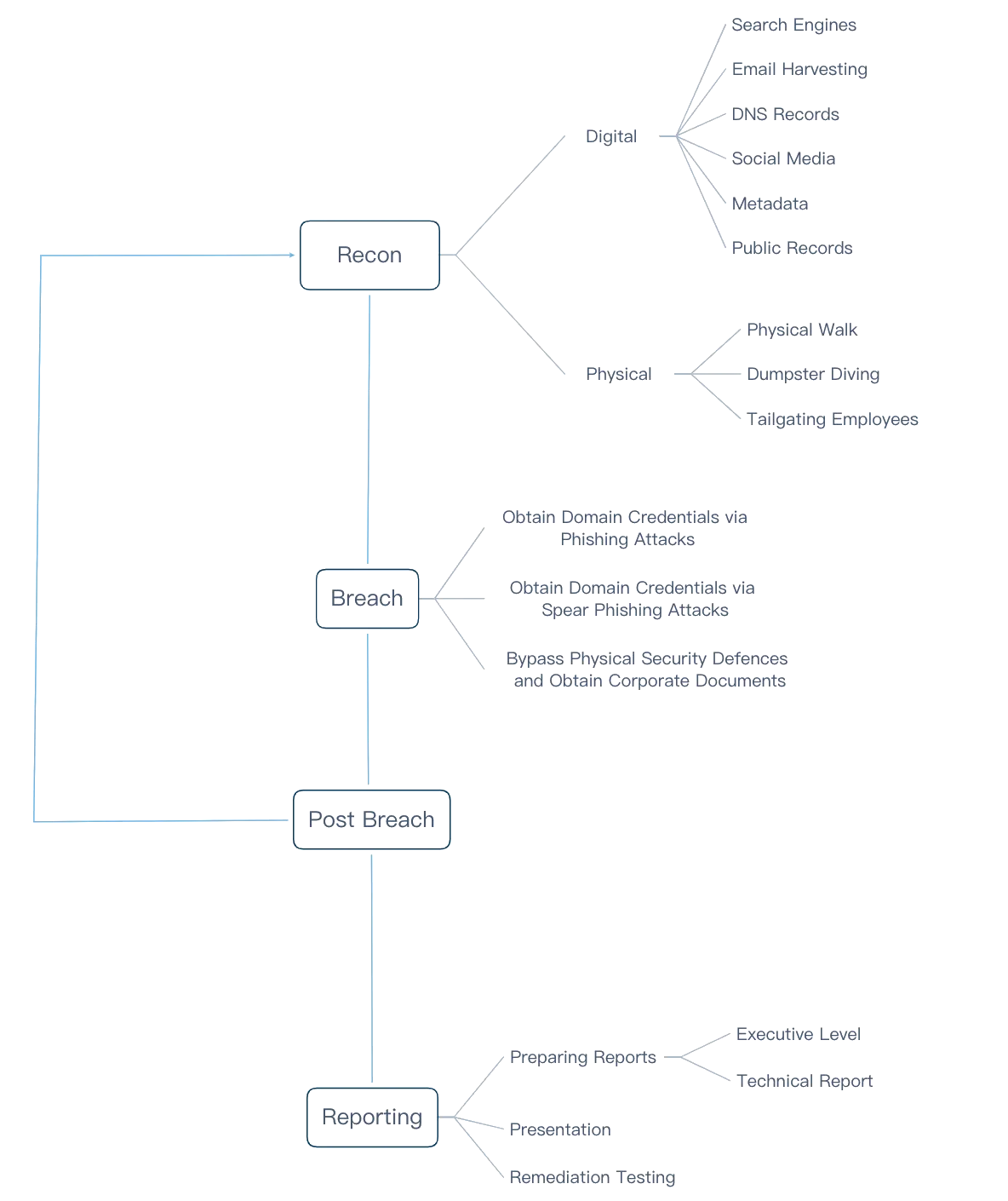
Introduction
Our Social Engineering Vulnerability Assessments are designed to lower this risk by identifying weaknesses that could allow attackers to target unsuspecting or uninformed employees. We conduct these tests using the tactics of social engineering, such as deception, manipulation, and intimidation, to see whether we can get the people in your organization to accidentally compromise your information.
Methodology