Introduction
Network Architecture Review undergoes quite a few technical and high-level assessments to get hold of the various possible flaws within the network.
This exposure is brought about by surveying the overall network design of a system, including personnel, processes as well as technologies.
Intect's methodology ensures that your network is safe from a security perspective.
Firewall Security Review can improve your ability to locate weaknesses in your network security posture and allow you to find where your policies need to be changed. In addition, they can assist you in demonstrating due diligence in reviewing your network security and policies in the event of a lawsuit or other issue which may question your security standards.
Methodology

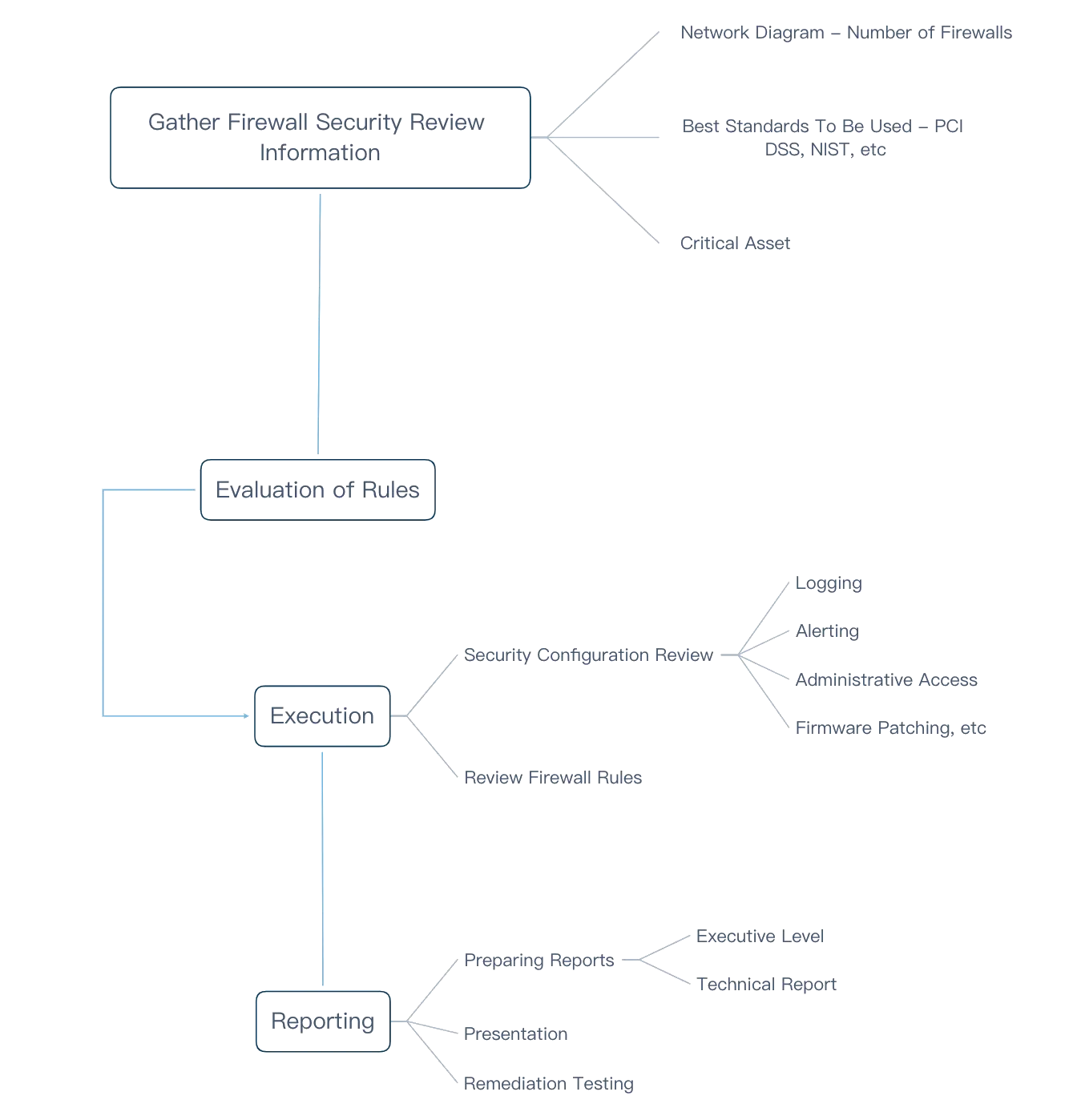
How It Works?
The technical aspect of the configuration and rule set, including syntax.
The business aspect of the rule set, involving allowed and disallowed activity.
Device management, including the authorization process.
Once we’ve examined the syntax of your configuration file and rule set to verify accuracy, we document your rule set with explanations in both technical and non-technical terminology. We also review your device management to make sure that it complies with best practices and regulatory guidance.