Introduction
Our team goes beyond the scope of OWASP Top 10 and performs an assessment that pushes the boundary for application security. We don’t solely scan the application for known bugs but leverage extensive research to identify deep technical vulnerabilities.
01
Bypassing Authentication
02
Escalating Privileges
03
Accessing Sensitive Data
04
Disrupting Legitimate Use
05
Gathering Intelligence
06
Manipulating Information
07
Manipulating Business Processes
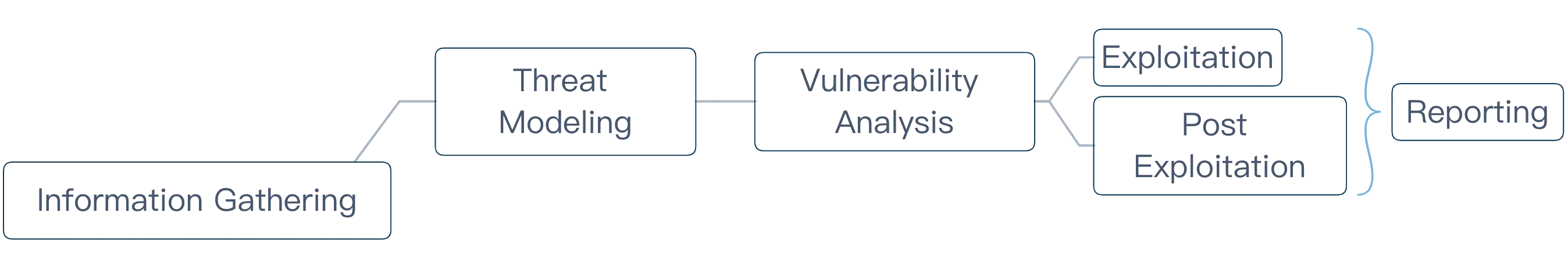
Methodology
Automated
Intect will identify the vulnerabilities present in the application with the help of automated tools and eliminate the false-positives. Automated scanners will give us an overview of the possible existence of vulnerabilities in the environment.
Manual
Our analyst will identify every exploitable vulnerability present in the application. We will check for logical flaws which might compromise authentication/authorization, injection attacks, data security, input validations, session management issues, etc. We also fetch every open port and the services running on the APIs’ servers. After that, we test them for vulnerabilities depending on their level of exploitability and availability on the environment they exist.
Types of Testing
Black Box
Black-box testing is a method of software/application testing that examines the functionality of an application without knowing it’s internal/backend working. It requires no prior knowledge of the application or the intervention of the application vendor.
Grey Box
In grey-box assessment, typically, the auditor has some knowledge of the application which is given by the business owners in form of application walk-throughs, application data flow, API documentation, etc. The purpose of grey-box assessment is to provide a more efficient & focused security assessment
Security Controls
| Data in Transit | The controls in this group protects the security of data in transit by mapping controls related to encryption and SSL/TLS protocols such as HTTPS, FTP, etc. |
| User Input Handling | The vulnerabilities in this group covers the security of the data against the malicious user inputs. |
| Business Logic Flaws | The vulnerabilities in this group are checked against the misuse of an application by circumventing the business rules i.e ways of using legitimate processing flow of an application in a way that results in a negative consequence to the organization. |
| Access Control | The authorization and the business logic decisions in the application are evaluated based on the controls in this group. |
| Authentication & Authorization | The controls in this group evaluates the application against weak passwords, insecure password recovery mechanisms, poorly protected credentials or lack of granular access control to access a particular interface. |
| Password Management | The controls in this group evaluate the practices implemented for storing and managing passwords to prevent unauthorized access. |
| Session Management | Controls in this group cover anything from how user authentication is performed, to what happens upon them logging out. |
| HTTP Security | Controls in this group evaluates the usage of various HTTP methods whenever data is sent to or received from the application server. |
| Data Protection | Vulnerabilities in this group covers the validation of the data sent to or received from the server along with the validation of the data stored at client side. i.e user PII information, key exchange, data tampering, etc. |
| Data Validation | The vulnerabilities in this group checks for the business logic decisions based on user input in the application. |
| Error Handling | The error handling section covers the information disclosure vulnerability arises due to the lack of user input sanitization. |